Introduction
In this post I’ll go through interesting URL submitted I saw on the any run public submission.
Hunting the source
hxxps://pub-e03b84ede40949d783b7ef41e8b36c50[.]r2[.]dev/web.html#REDACTED@syriatel[.]com.sy
when visiting the URL it looks like an Outlook login page with the prefilled email address REDACTED@syriatel[.]com[.]sy which is written in the URL after the [#] character (I think this email received the spam email that led to the phishing site).
The view source is disabled so I inspect the HTTP request using burp after refreshing the page
Basic Malware RE
The room link : Room link
Strings : Challenge 1
Lets start the first task
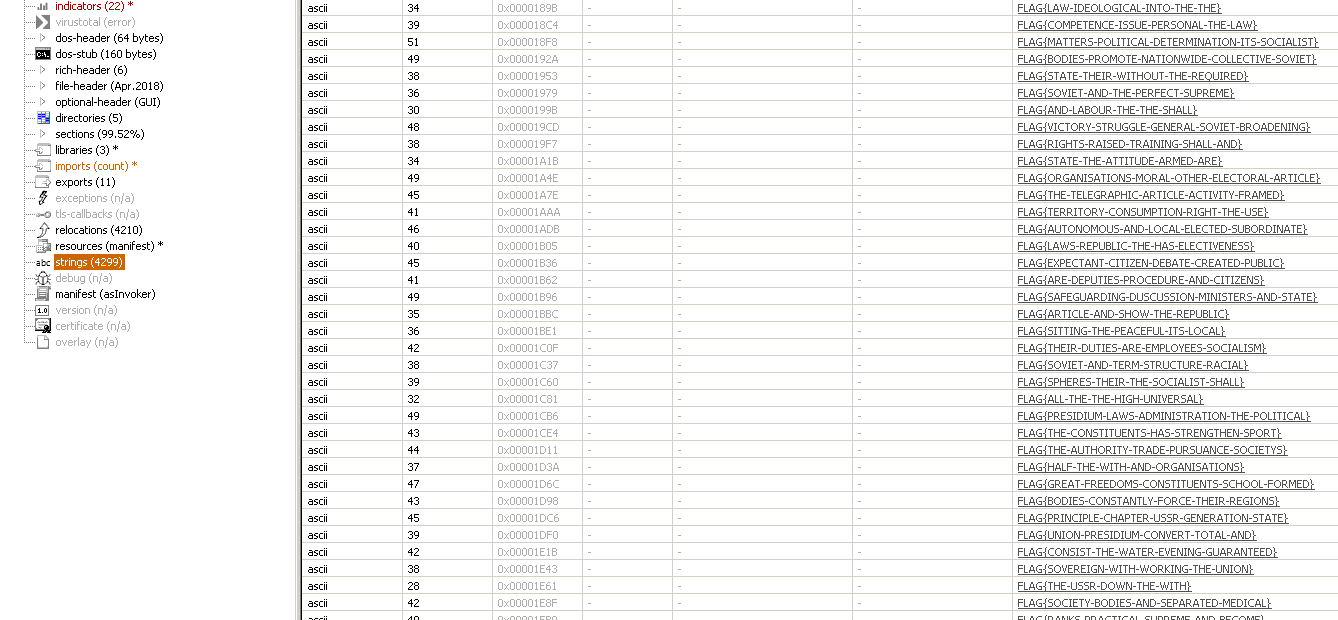
let’s download the file then use PE-studio, because of the name of the task “string” I thought it was about strings so immediately I went to the strings part in pe studio and we can see there are a lot of them
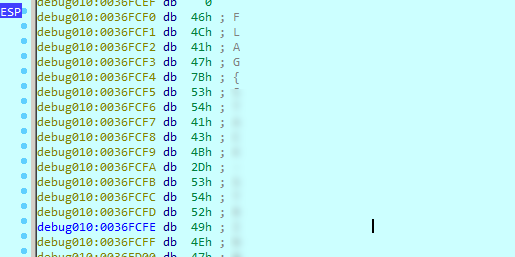
let’s drag the file into our favorite tool IDA
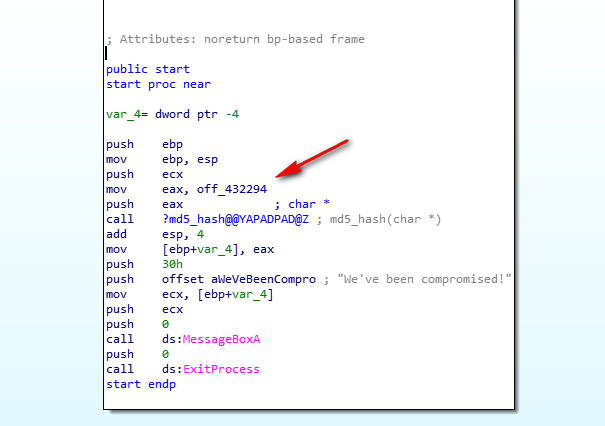
it is obvious that what is stored in off_432294 is pushed as a parameter for the md5_hash function (it prints generated md5 in the message box)
so just go to off_432294 and here is your flag
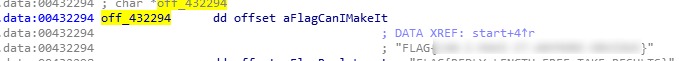
Strings : Challenge 2
this time lets start by open the task file using IDA
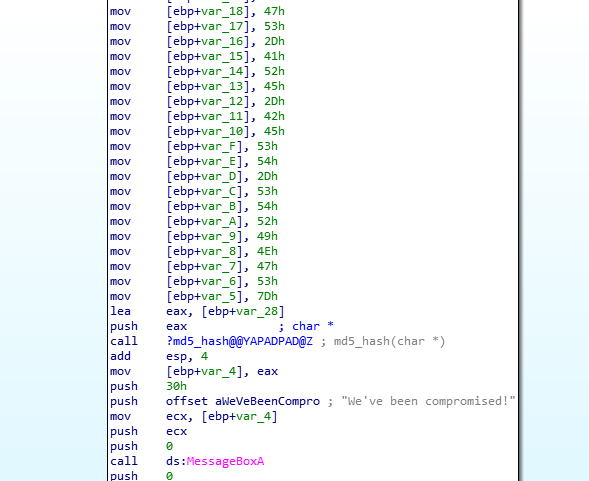
we can see a lot of values are pushed to the stack before calling the md5 function the solution is very easy and there is more than one way to solve it, but because I’m too lazy to open any other tool.
I’ll debug the file using ida and put a breakpoint before the calling instruction, Then I’ll extract the values from the stack.
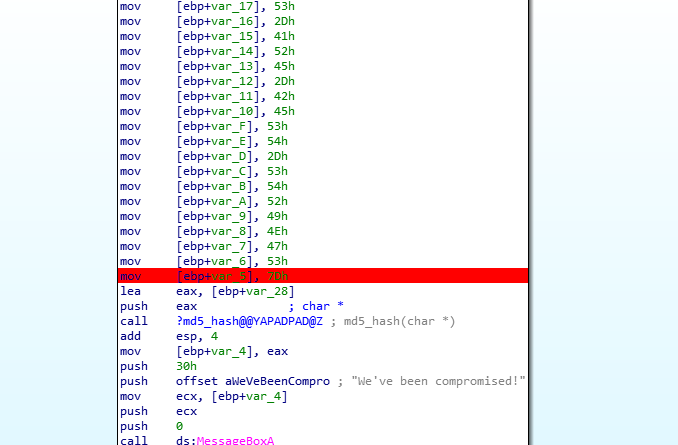
now we can see our dear flag in the stack